Cybersecurity Consulting
SeattlePro has been offering cybersecurity consulting for almost two decades to businesses across the United States. During this period, as new technologies have emerged, the cybercrime has evolved, and cybercriminals have discovered new ways to attack organizations using social engineering, ransomware, and other techniques.
The cybercrime statistics are mind-boggling. The top issues faced by governments, businesses, and individuals today are the cybersecurity risks and threats. The countries are replacing traditional military attacks with cyberattacks, which is increasing the demand for cybersecurity professionals. SeattlePro’s network security audit and other cybersecurity services are designed to secure your business infrastructure.

Why Should Cybersecurity Be a Top Priority?
|
SeattlePro consultants have decades of experience in cybersecurity consulting and training. We can help your organization address the cybersecurity concerns that are specific to your business.
Cybersecurity Strategy
Cybersecurity is our specialty. Our cybersecurity experts specialize in vulnerability assessment, risk assessment, business continuity, and penetration testing. We can help you develop a cybersecurity strategy that’s tailor-made for you.
Network Security Audit
In addition to a Basic Network Security Audit, we also offer a more Comprehensive Network Security Audit, which examines your entire corporate network infrastructure and includes your business processes.
Enterprise Security Risk Assessment
The goal of our security risk assessment is to understand your existing business environment, identify the risks through analysis of the information that we collect, and then use the data to effectively mitigate the risks.
Security Awareness & Training Program
Humans are the weakest cybersecurity link. Therefore, implementing a security awareness and training program is key to securing your organization’s valuable assets and protecting your intellectual property.
Cybersecurity Strategy & Approach
Our goal is to help your organization protect your valuable business assets from cyberattacks and ensure business continuity. No two networks are alike, and we believe that the cookie cutter approach to solving complex problems doesn’t work. The cybersecurity solutions are not always straightforward and therefore the cybersecurity strategy must be unique to each business based on the network infrastructure in place, the type of business, geographical location, security culture, and the technologies in use.
SeattlePro will work with your Information Security staff to devise a cybersecurity strategy that fits your business needs, adheres to your company policies, and complies with the industry regulations. We will then implement security controls based on National Institute of Standards and Technology (NIST) recommendations and other industry standards. Implementing a solution that’s based on well-known standards and regulatory requirements and coupling it with our vast experience and best practices, will be instrumental in securing your business infrastructure. In addition, our cybersecurity consultants will also guide you through the implementation of a Security Awareness and Training Program that will help you stay secure in the future.
SeattlePro’s certified cybersecurity consultants hold many popular security certificates, such as:
- Certified Information Systems Security Professional (CISSP)
- Certified Ethical Hacker (CEH)
- Computer Hacking Forensic Investigator (CHFI)
- Certified Network Defense Architect (CNDA)
- GIAC Security Essentials (GSEC)
- EC-Council Certified Security Analyst (ECSA)
- Certified Information Security Manager (CISM)
- Certified Information Systems Auditor (CISA)
- Systems Security Certified Practitioner (SSCP)
- GIAC Penetration Tester (GPEN)
- CompTIA Security+

Network Security Audit
We can customize the security audit, depending on your organization’s needs and requirements. The two most popular types of security audits we offer are the Basic Network Security Audit and the Comprehensive Network Security Audit. However, we can do other types of security audits which are specific to certain areas of your network. Some examples of these audits include:
- Operating System Audit
- Application Audit
- Identity & Access Audit
- Wireless Network Audit
- Remote Connectivity Audit
- Active Directory Audit
- Cloud Security Audit
- Physical Security Audit
- Information Security Policies Audit
SeattlePro’s Basic Network Security Audit gives an organization a higher-level view of the current state of their network. The basic audit is essentially a subset of our comprehensive security audit, but our audit report will still give you a good sense of whether your organization is relatively secure and what basic improvements are necessary to enhance your company’s security posture. At the end of the audit, we provide a Network Security Audit Report to give your executives a better picture of the overall network security status.
Our Comprehensive Network Security Audit includes a much more detailed audit of your entire network that encompasses hardware, software, information handling, and user practices. We not only look at how your employees access and share data with other employees, we also look at how the external users, such as contractors, business partners, and vendors interact with your network and employees. Our audit covers firewalls, network protocols and services, Windows servers, client workstations, wireless network, physical security and much more. We look at your organization’s Active Directory design, configuration, and security settings; Group Policies, windows registry settings, desktop client configurations, Web browsers setup, and other areas that may pose a security risk to your network. In addition, we also examine your business culture, processes, policies, procedures, and security controls that are in place. At the end of the audit, we provide a fairly detailed Network Security Audit Report, which is helpful to your senior executives and network administrators.
If the network security audit reveals any security risks, vulnerabilities, or other areas of concerns, we can work with your Information Security staff to plug the security holes, protect the information systems and devices, and train your IT staff and information workers so your organization is better equipped to defend against potential cyberattacks in the future.
Enterprise Security Risk Assessment
An enterprise security risk assessment not only helps an organization assess and identify important business assets, it is also useful in determining the value of its data and the different types of information that is stored on-premises or in the cloud. Without enough knowledge of the type of data that belongs to an organization, it’s difficult to decide how to prioritize and allocate appropriate resources to secure corporate assets.
There are many reasons why an organization might want to protect its business information. Whether the information security is mandated by legal or regulatory reasons, or a corporation wants to secure its intellectual property from hackers and adversaries, an enterprise security risk assessment by SeattlePro cybersecurity professionals can help in identifying the risks to your business assets. We can then assist you in mitigating those security risks.
Information Systems Audit and Control Association (ISACA) recommends an enterprise security and risk assessment at least every two years.

Security Awareness & Training Program
SeattlePro’s Security Awareness & Training Program is based on NIST Special Publications 800-50 and 800-16. These guidelines are used by federal agencies in the United States. The recommendations emphasize the importance of the “people factor”, which are key to providing an appropriate level of security to the organization but recognizes that people are also the weakest link in securing systems and networks.
SeattlePro’s Security Awareness & Training Program is vital to ensuring that your employees adhere to organizational policies and know how to use and protect your corporate assets. A successful implementation of security awareness program will play an important part in enhancing the security culture of your organization.
The scope of our Security Awareness & Training Program is enterprise-wide and ensures that employees from every level are participating in the program: information workers, supervisors, managers and senior executives. If your organization works with contractors, vendors, and temporary employees, we will also include them in the security awareness program, if necessary. This will ensure they too are aware of your security policies and procedures and know how to handle your corporate data properly.
We use a methodical approach to design, develop, implement, and maintain a security awareness and training program, which includes several key steps. There are three major steps in the development of the security awareness program: design, development, and implementation.
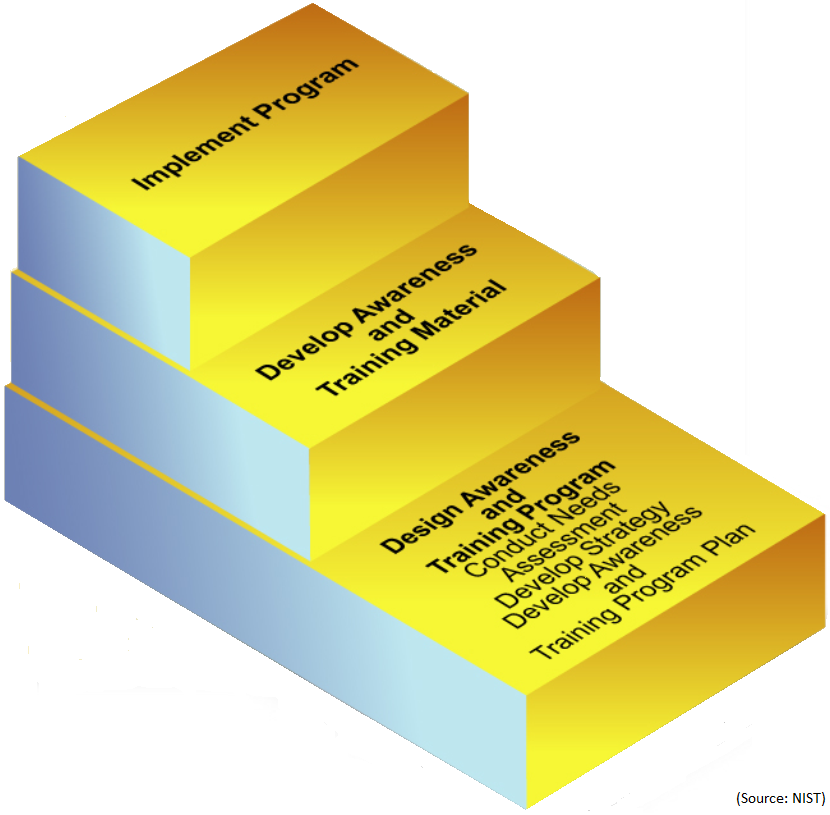
Each major step is then further broken down into minor steps, based on the organization’s needs, geographical dispersion, size, and other factors. A typical security awareness program includes the following steps.
- Needs Assessment: Conduct a needs assessment for organization’s security awareness and training.
- Develop Strategy: Develop an awareness and training strategy and plan, which will not only include the scope, but also the roles and responsibilities of the personnel.
- Set Priorities: Establish a priority to determine which component will be scheduled first and in what sequence.
- Training Material: Determine the complexity of the material that will be developed.
- Fund Program: Funding the security awareness and training program.
- Implement Program: Once the above steps are complete, the program is communicated and implemented.
- Continuous Improvement: Ensure the program doesn’t become obsolete with time and continues to meet the overall objectives in the future.
Please contact us for more information about our cybersecurity consulting services.
