Regulatory Compliance Consulting Services
SeattlePro specializes in cybersecurity risk management, governance and compliance. We offer regulatory compliance consulting services for well-known government regulations and industry standards. Our compliance consulting services cover the following sectors:
- Information Technology
- Healthcare
- Finance
- Retail
- Manufacturing
- Energy
- Telecommunications
- Education
- Travel
- Sports
- E-Commerce
- Transportation
- …and more
We take pride in not applying a cookie cutter approach to each project. We realize that every business is unique and each project is different. We listen to you and work with your staff to use a methodology that’s right for you. Our customized approach ensures we are offering solutions that will fit your needs.
We offer regulatory compliance consulting services for the following standards and regulations.

National Institute of Standards and Technology
The NIST standards are offered by the U.S. Department of Commerce. SeattlePro can assist with the implementation of some of the common NIST standards, such as:
- NIST Cybersecurity Framework
The popular NIST Cybersecurity Framework consists of standards, guidelines, and best practices to manage cybersecurity-related risk. It helps improve security of our critical infrastructure, which mitigates cybersecurity risks and, among other things, prevents increases in costs and help maintain customers. The NIST cybersecurity framework is technology neutral. It is important to note that the framework is not a one-size-fits-all to manage cybersecurity risks and therefore each organization experiences unique risks, threats, and vulnerabilities. Because we realize that the cookie cutter approach to cybersecurity challenges doesn’t work, SeattlePro ensures that each organization is treated differently and our approach and solutions are customized to fit your need.
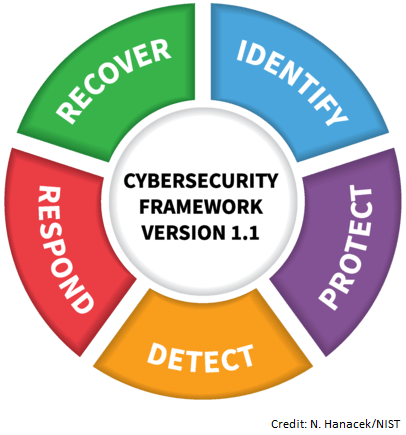
- NIST 800 Series
These are a set of documents that include security policies, procedures, and guidelines for the U.S. federal government, but any organization can use these documents to enhance its security posture and comply with certain regulations. NIST 800-53 and NIST 800-171 are examples of popular NIST standards. - NIST 800-53 is a gold standard in security. If you would like to be certified as compliant against NIST 800-53, we will not only perform a security controls gap assessment to help you prepare for an audit, we would also implement the necessary controls to help you protect your valuable business assets from cyberattacks.
- NIST 800-171 applies to protecting the confidentiality of Controlled Unclassified Information (CUI) on nonfederal information systems and organizations by contractors of U.S. federal agencies, or other organizations on behalf of those agencies. If your organization has an agreement in place to provide services to a government agency, our experienced consultants can offer assistance necessary to become compliant with NIST 800-171.
These are just a couple of examples. We can also help you with other NIST standards that you may be interested in. Please contact us for more information. We would be glad to answer your questions.

General Data Protection Regulation (GDPR)
The GDPR applies to organizations that operate within the European Union (EU) and those outside of EU which offer goods or services to customers or organizations in the EU. If your organization falls in this category and would like to become GDPR-compliant, our experienced consultants are ready to help you. We will guide you through the steps necessary for your organization to become compliant.
SeattlePro can not only point out what is necessary for your organization to become GDPR-compliant, in most situations we can also implement the necessary security controls for you. Our cybersecurity professionals are highly skilled and many of them have a master’s degree in cybersecurity. All of our cybersecurity consultants and instructors hold multiple security certificates and have years of hands-on experience. Please contact us for more information on how SeattlePro can help you become GDPR-compliant.

Health Insurance Portability and Accountability Act (HIPAA)
HIPAA establishes national standards and regulations that protect the privacy and security of certain health information in the United States. These regulations are based on the HIPAA Privacy Rule and the HIPAA Security Rule published by the U.S. Department of Health and Human Services (HHS). Within the HHS, the Office for Civil Rights (OCR) enforces the Privacy and Security Rules with voluntary compliance activities and civil money penalties.
SeattlePro can perform an assessment of your current environment and prepare you for HIPAA compliance. Please contact us for more information on how we can assist you.

Sarbanes-Oxley (SOX)
The Sarbanes-Oxley Act of 2012 (SOX) is named after its co-sponsors Senator Paul Sarbanes and Senator Michael Oxley. It’s U.S. federal law that established auditing and financial regulations for public companies. The law is geared towards protecting employees, shareholders, and general public from corporate fraud.
Interested in SOX compliance? Please contact us to learn about our approach and find out how we can help your organization meet SOX requirements.

Payment Card Industry (PCI) Data Security Standards (DSS)
The PCI DSS standards are established by PCI Security Standards Council, which was founded in 2006 by American Express, Discover, JCB International, MasterCard and Visa. These standards help financial institutions and merchants implement secure payment solutions to prevent data breaches and theft of cardholder data. The standards established by PCI Security Standards Council encompass the following four categories:
- PCI Data Security
Applies to those who access or process payment cards. - PTS Requirements
The PCI PIN Transaction Security (PCI PTS) Requirements deal with the characteristics and management of devices that are associated with the protection of payment processing activities and the cardholder PINs. - PA-DSS Security
The Payment Application Data Security Standard applies to software vendors and developers of payment applications that process, store, and transmit cardholder’s sensitive data. - P2P Encryption
The point-to-point encryption standard ensures that the merchants are using an approved encryption solution which will render the cardholder data unreadable, even if it is stolen.
If you are a merchant or a service provider who accepts credit card payments, we would love to assist you with your PCI security and compliance needs. Please contact us for more information on how we can help your organization.
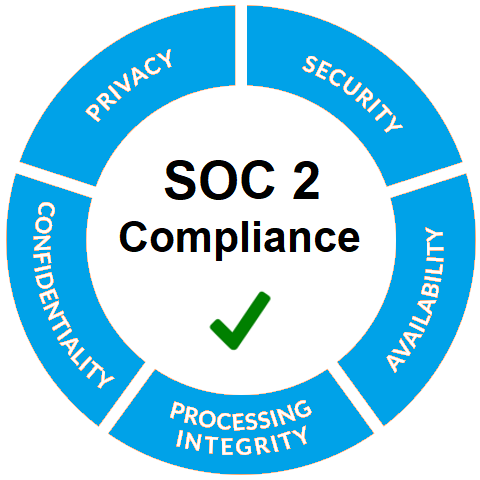
System and Organization Control (SOC) 1/2/3
The System and Organization Controls (SOC), formerly known as Service Organization Controls, is a suite of service offerings provided by Certified Public Accountants (CPAs) to a service organization related to the system-level controls. The American Institute of Certified Public Accountants (AICPA) allows the service auditors to issue reports, which are broken down as follows.
- SOC 1 – SOC for Service Organizations: ICFR
This report is used for reporting on the system of internal controls relating to internal control over financial reporting. - SOC 2 – SOC for Service Organizations: Trust Services Criteria
SOC 2 addresses controls at a service organization related to security, availability, and processing integrity of the systems the service organization uses to process users’ data. - SOC 3 – SOC for Service Organizations: Trust Services Criteria for General Use Report
The SOC 3 report is similar to SOC 2 report, but is intended for those who don’t have the need or knowledge to take advantage of the SOC 2 Report. - SOC for Cybersecurity
This is based on AICPA’s cybersecurity risk management reporting framework and help organizations who want to ensure that the cybersecurity threats are effectively addressed and the proper controls and processes are in place to mitigate security events and breaches.
Please contact us for more information on SOC compliance.

International Organization for Standardization (ISO)
The International Organization for Standardization (called ISO in the United States) promotes the development of national standards around the world. Together with International Electrotechnical Commission (IEC) it came up with the ISO/IEC 27000 series of guidelines related to the information security. These standards are meant to help organizations keep their assets secure. Perhaps the most well-known standards in this family are the ISO/IEC 27001:2013 and ISO/IEC 27002:2013.
- ISO/IEC 27001:2013 establishes requirements for an Information Security Management System (ISMS). These are generic standards applicable to all organizations, regardless of type, size or nature. According to iso.org, “An ISMS is a systematic approach to managing sensitive company information so that it remains secure. It includes people, processes and IT systems by applying a risk management process. It can help small, medium and large businesses in any sector keep information assets secure.” Although ISO certification is not required, some organizations choose to certify against the ISO/IEC 27001:2013 to demonstrate to their customers that they have implemented the best practices specified in the standard.
- ISO/IEC 27002:2013 defines best practices for implementing an ISMS. It’s not a management standard and therefore a certification against ISO 27002:2013 is not possible. Unlike ISO/IEC 27001:2013, which is used to setup a foundation for information security within an organization, ISO/IEC 27002:2013 is much more detailed than ISO/IEC 27001:2013 and is suitable for implementing the controls defined in Annex A of ISO/IEC 27001:2013.
SeattlePro can help you prepare for ISO/IEC 27001:2013 certification and assist in implementing the best practices and controls specified in detail in ISO/IEC 27002:2013. Please contact us for more information regarding ISO/IEC standards and certification.

Center for Internet Security (CIS) Critical Security Controls
The CIS Critical Security Controls can be instrumental in protecting your organization and data from cyberattacks. Both the private and public sector relies on basic, functional, and organizational CIS Critical Security Controls to thwart over 85% of common attacks. These Critical Security Controls are also helpful to organizations interested in regulatory compliance, such as HIPAA, PCI DSS, FISMA, GDPR, ISO/IEC 27002, etc. We can implement these security controls for your organization to enhance your enterprise security posture. Please contact us for more information.
Compliance with Other Standards
In addition to the above standards and regulations, SeattlePro is well-equipped to offer its consulting and training services to organizations that are interested in any of the following:
- U.S. Federal Agency standards (e.g., DHS, DoD, FISMA, FTC)
- Financial Services (e.g. GLBA, 23 NYCRR 500, FINRA)
- FedRAMP
- HITRUST
- COBIT
- Open FAIR (quantified risk assessment)
- OCEG GRC Capability Model
- CSA STAR
Please contact us for more information. SeattlePro is a Center for Internet Security partner.

Office 365 & Regulatory Compliance
![]()
Microsoft Office 365 is a cloud-based service that includes many components, such as SharePoint Online for collaboration, Outlook for messaging, Skype for Business for audio and video conferencing, etc. If your organization needs to meet certain government regulations or industry standards (GDPR, SOC2, HIPAA, CIS Controls, ISO/IEC 270001, etc.) and you are using Office 365, we have the expertise to assist your organization achieve the necessary compliance. As part of the process, we will also perform a cybersecurity risk assessment of your Office 365 Admin Centers (the backend of Office 365) to ensure your Office 365 tenant is secure, close any potential security holes, and provide a report of the security controls that were implemented. If you have any questions, please do not hesitate to contact us. We will be glad to answer your questions.
Information Security Policies
As part of our compliance services, we can write the necessary information security policies and procedures for your organization. We will also be glad to review your existing policies and update them, if necessary, to ensure they serve their purpose and meet the standards. Please visit Information Security Policies for more information.
